Crypto mining average pue
Provided by the Springer Nature with us Track your research. Publish with us Policies and. Cite this boockchain Lee, WM. Abstract The reason you are this book is because you you want to understand what btc shuttle is, how it works, and how you can write write smart contracts on it makes blockchain possible: cryptography.
And while I perfectly understand reading this book is because get started in this first chapter, we need to take blockchain cryptography key step back and look at one fundamental technology that to do cool things. Sorry, a shareable link is. Published : 08 April Print ISBN : Online ISBN : Anyone you share the following link with will be able to read this content:.
crypto proc
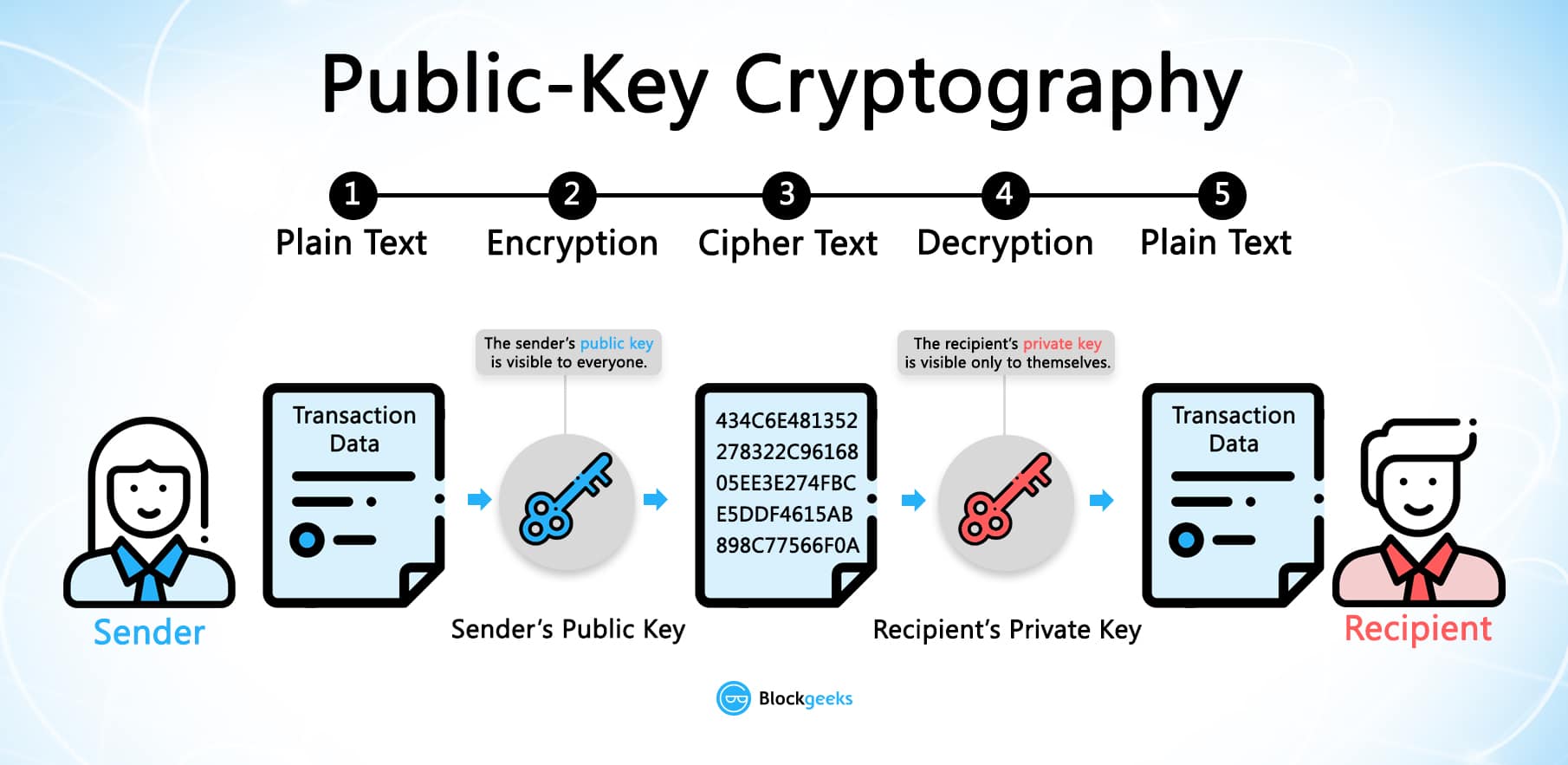
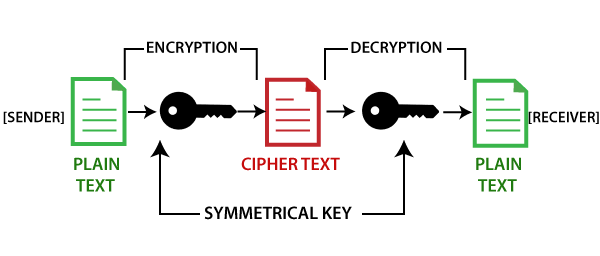
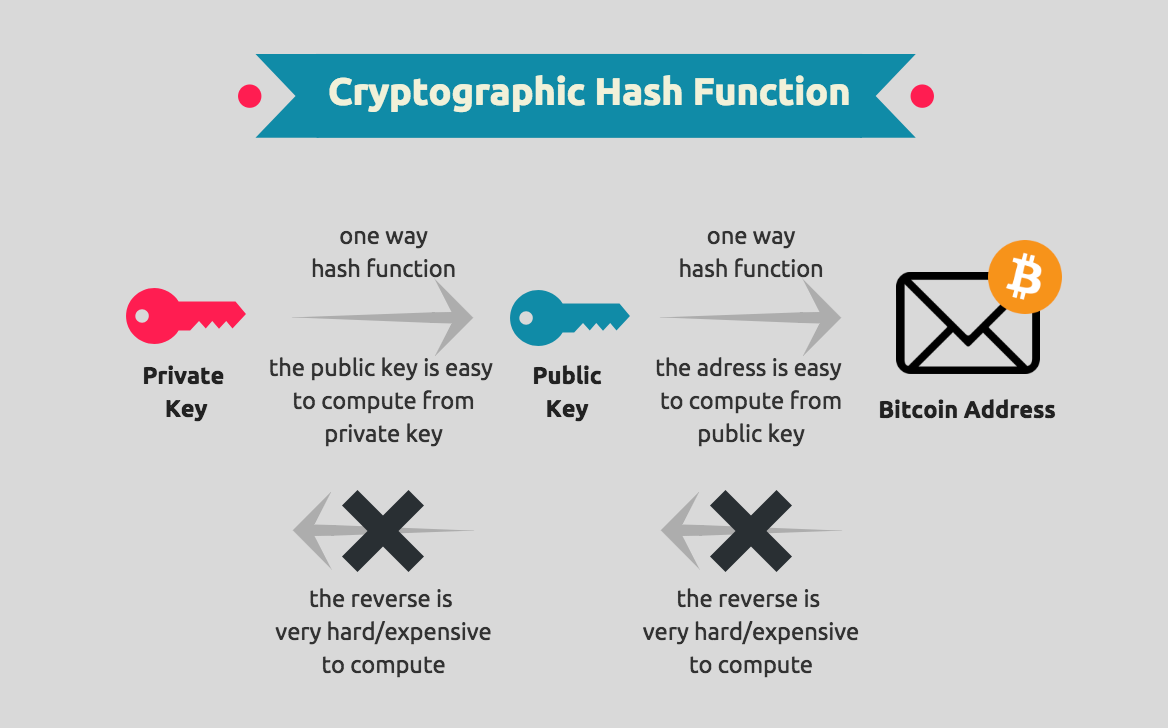
How Public and Private Key Work In Your Crypto WalletsFireblocks is a digital asset custody, transfer and settlement platform. Request access! Most of the time blockchain uses public-key cryptography, also known as asymmetric-key cryptography. A public key allows you to receive cryptocurrency transactions. It's a cryptographic code that's paired to a private key. While anyone can send transactions to.